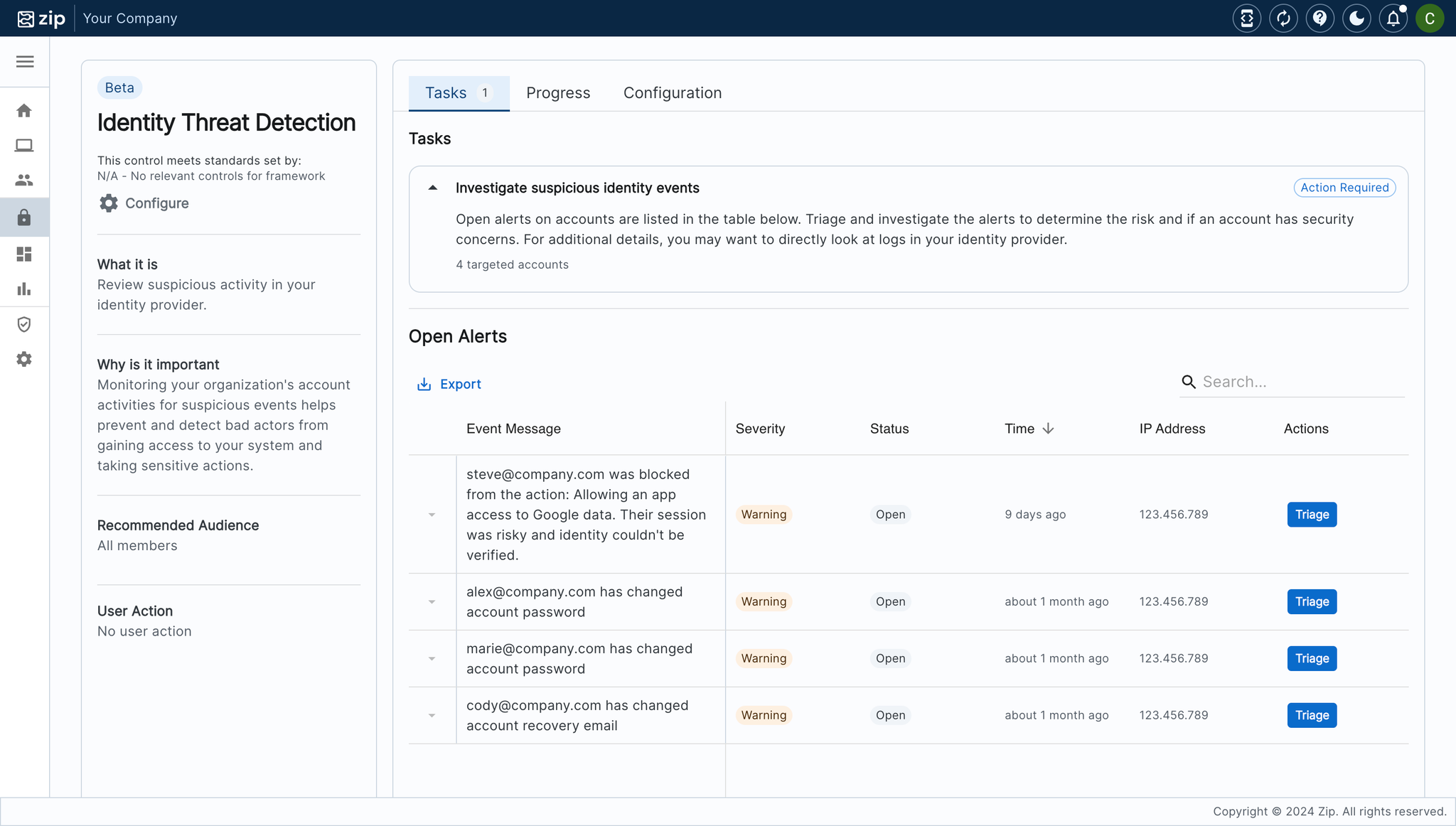
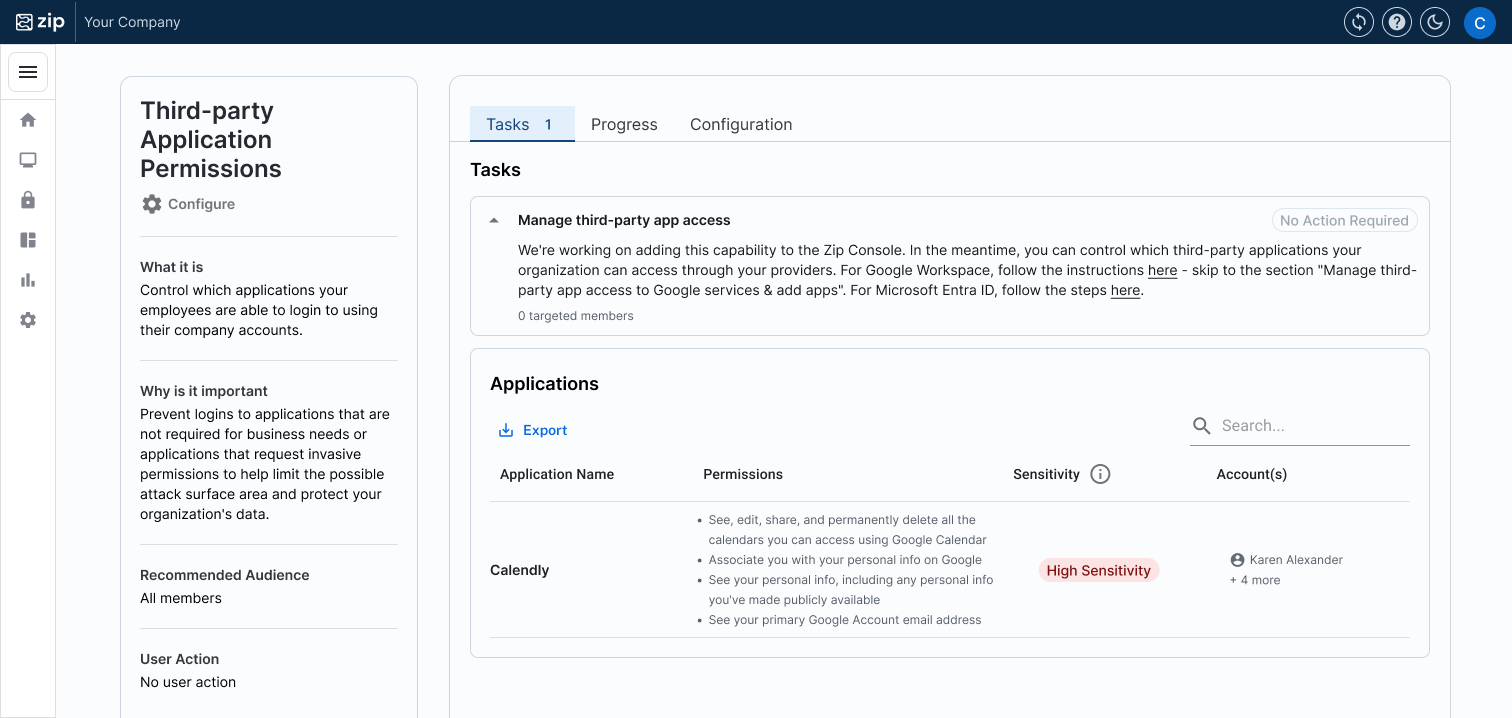
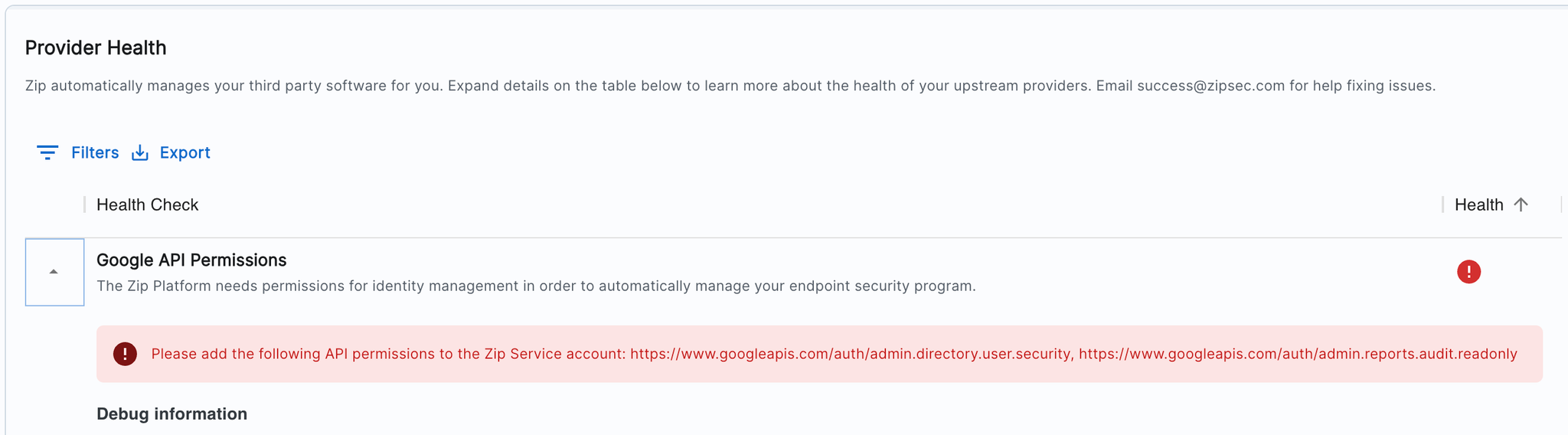
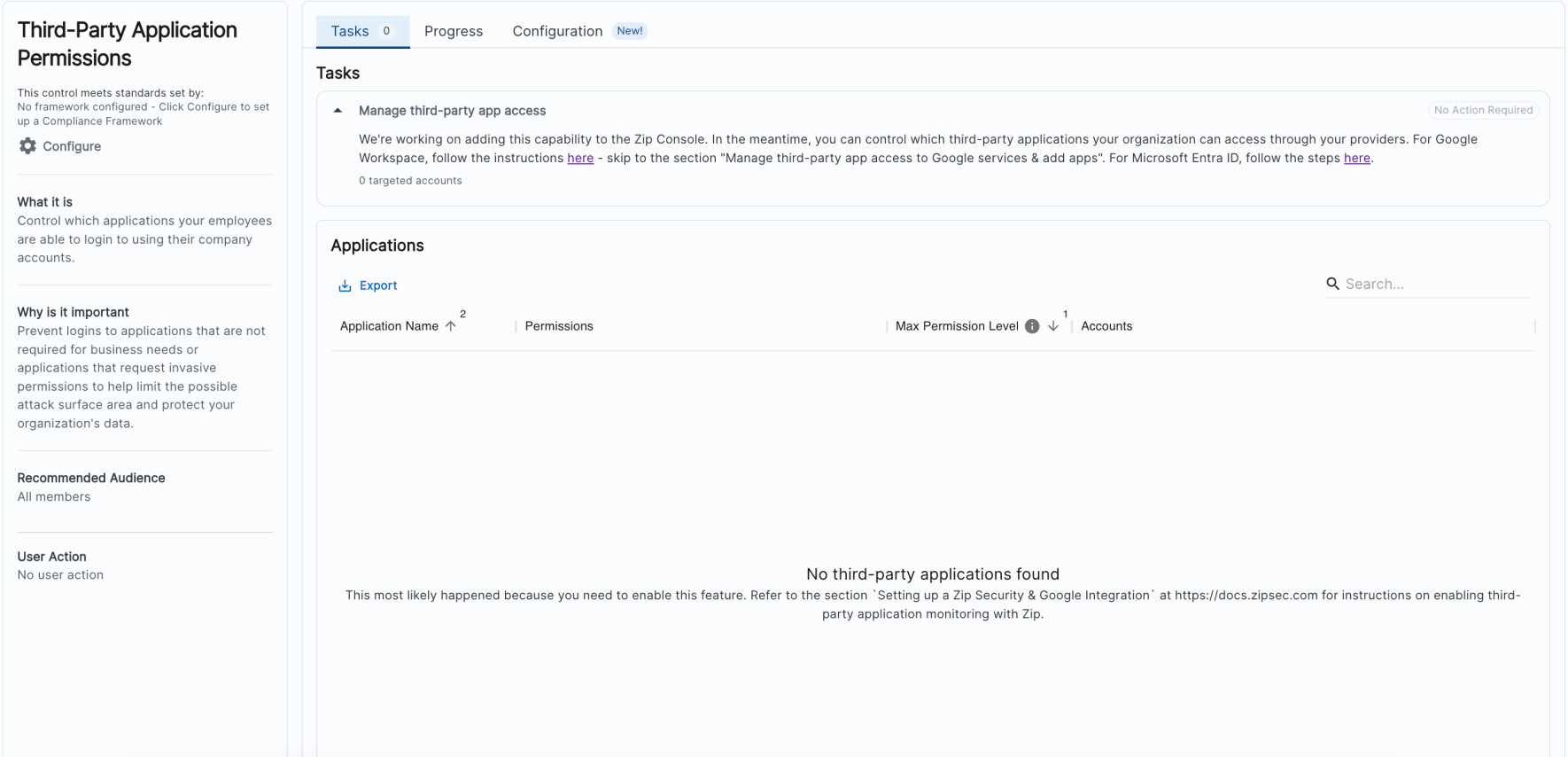
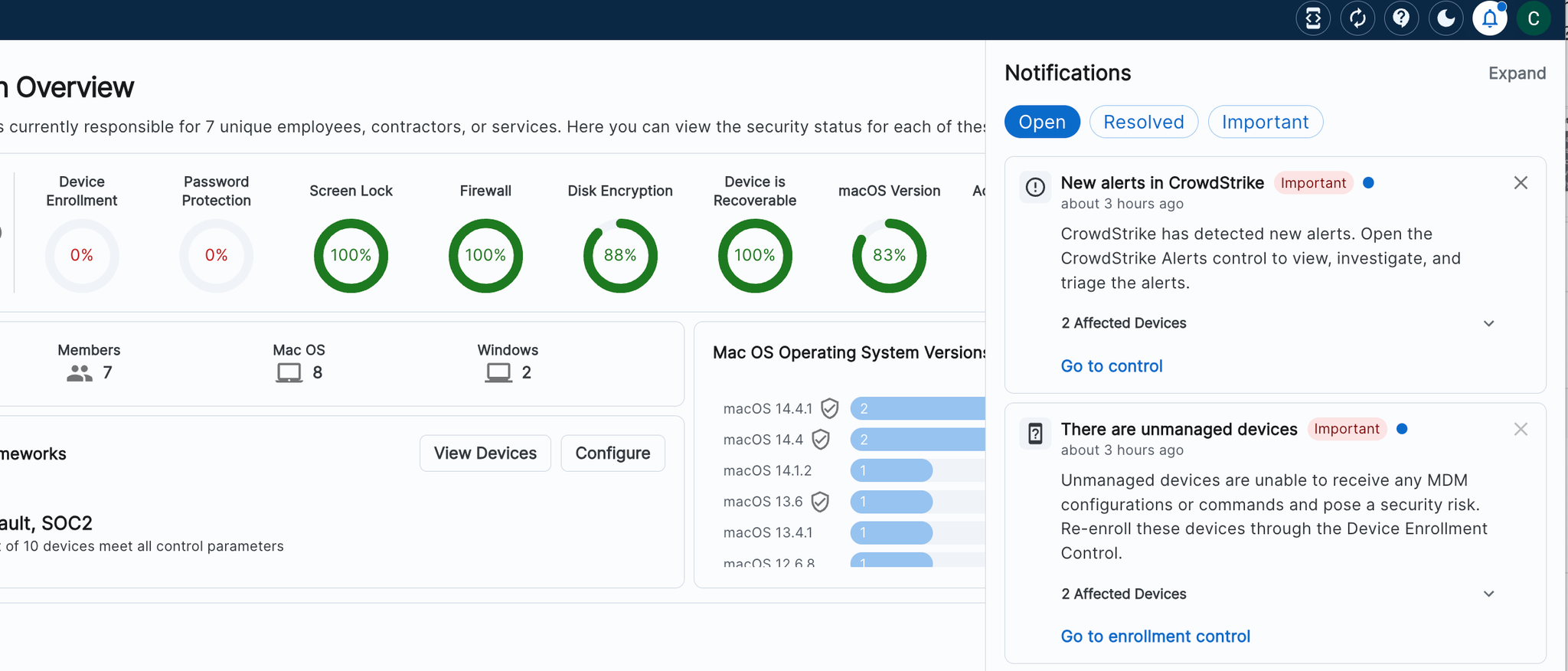
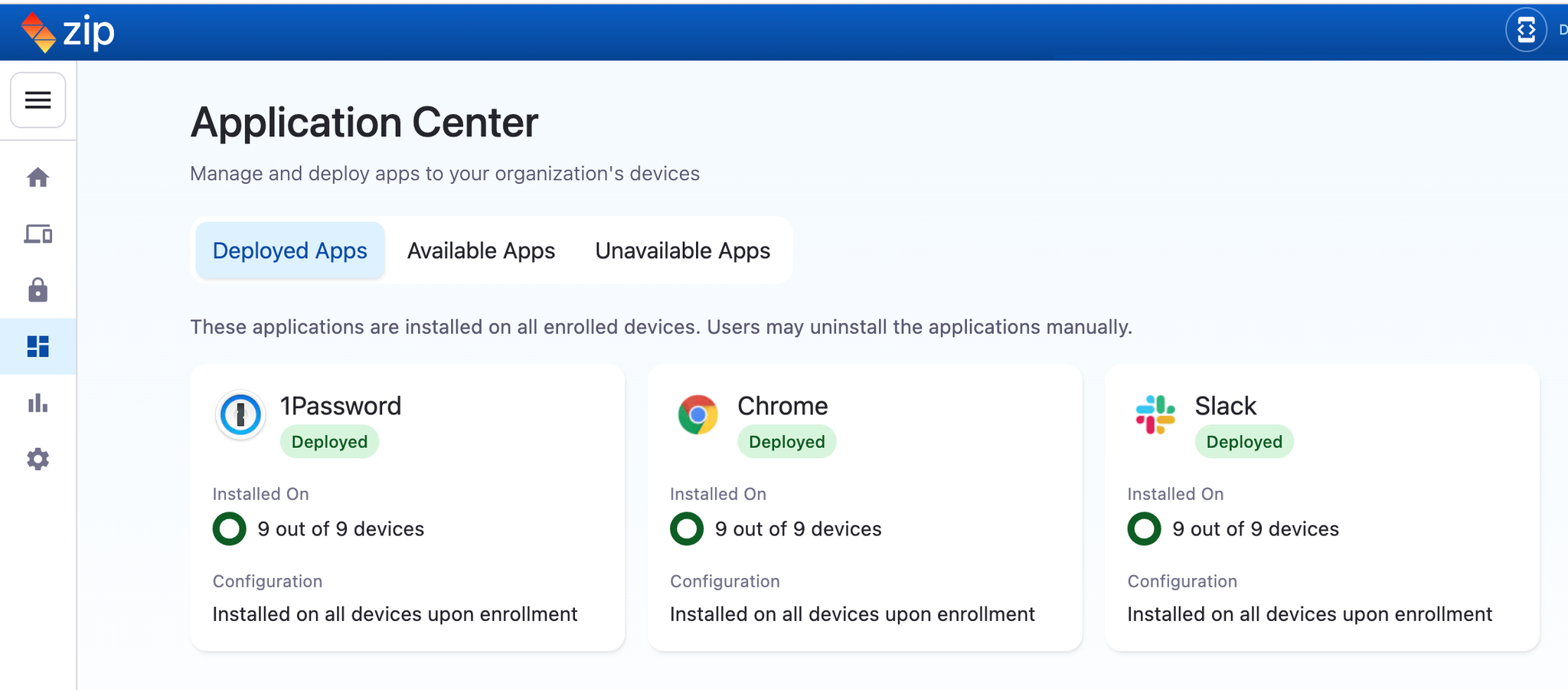
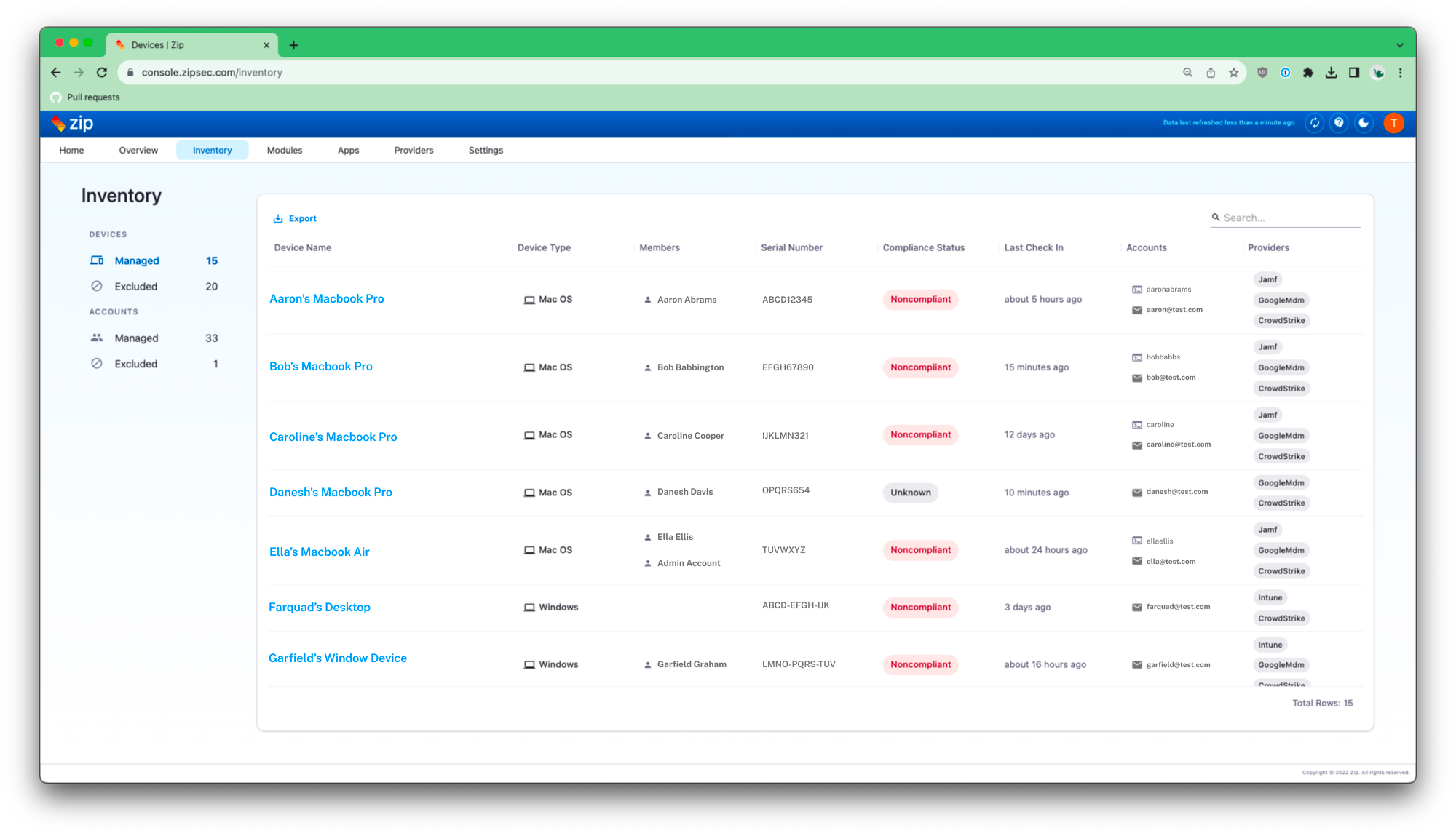
✨ Third-Party Applications Control
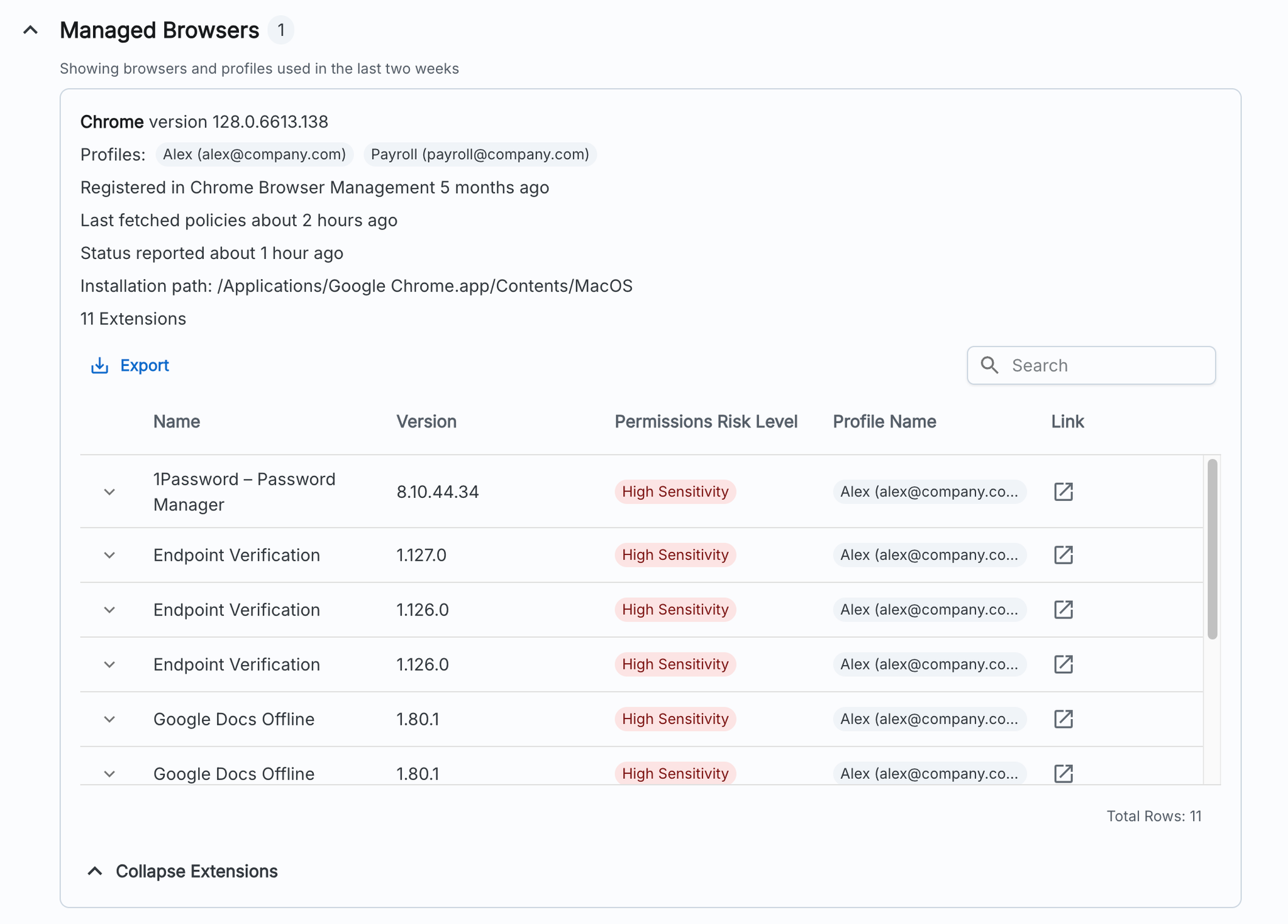
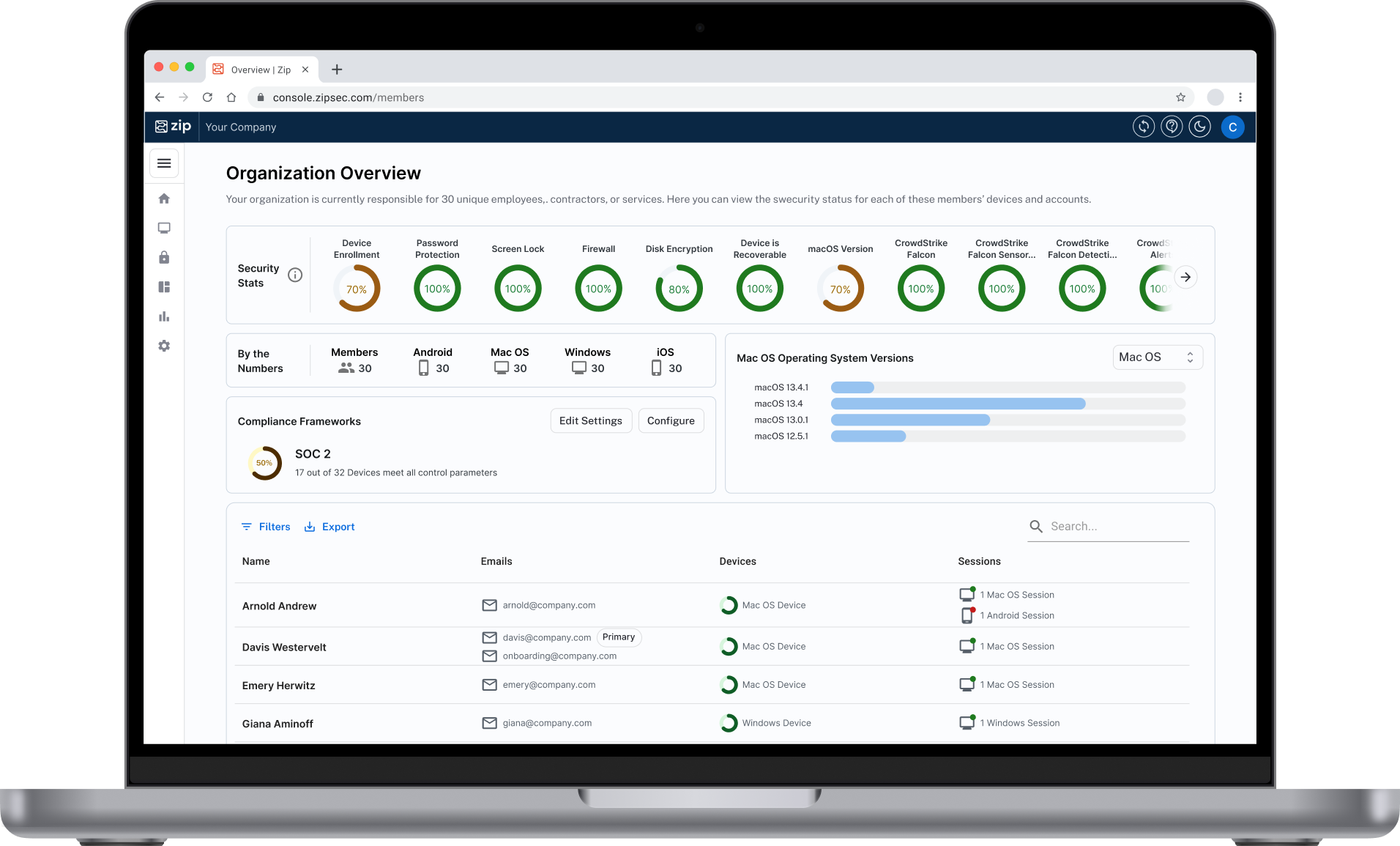
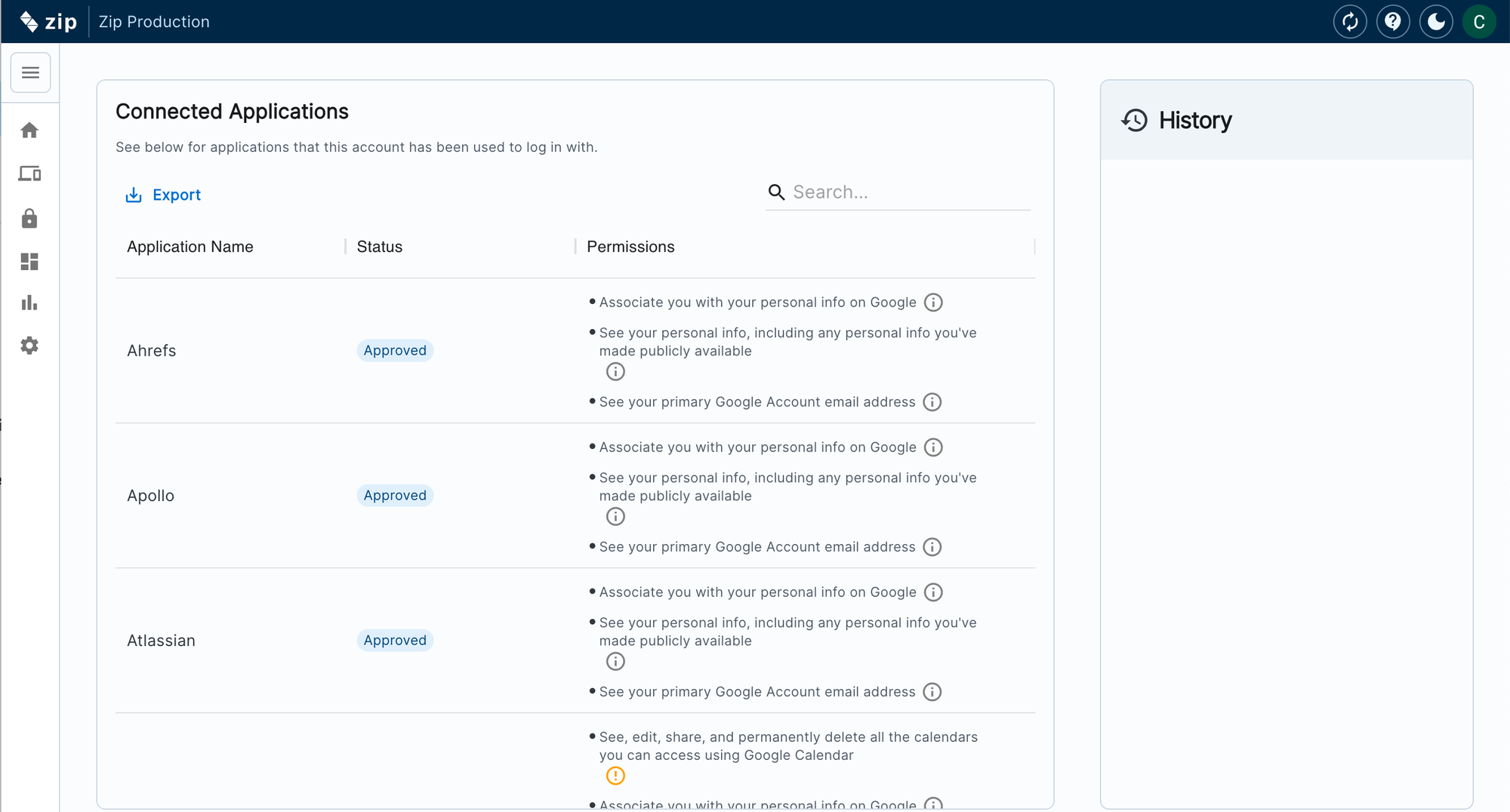
Our latest control, Third-Party Applications, gives you a clear view of the apps your employees have granted their corporate accounts access to. Employees often sign into SaaS apps through a flow like so:
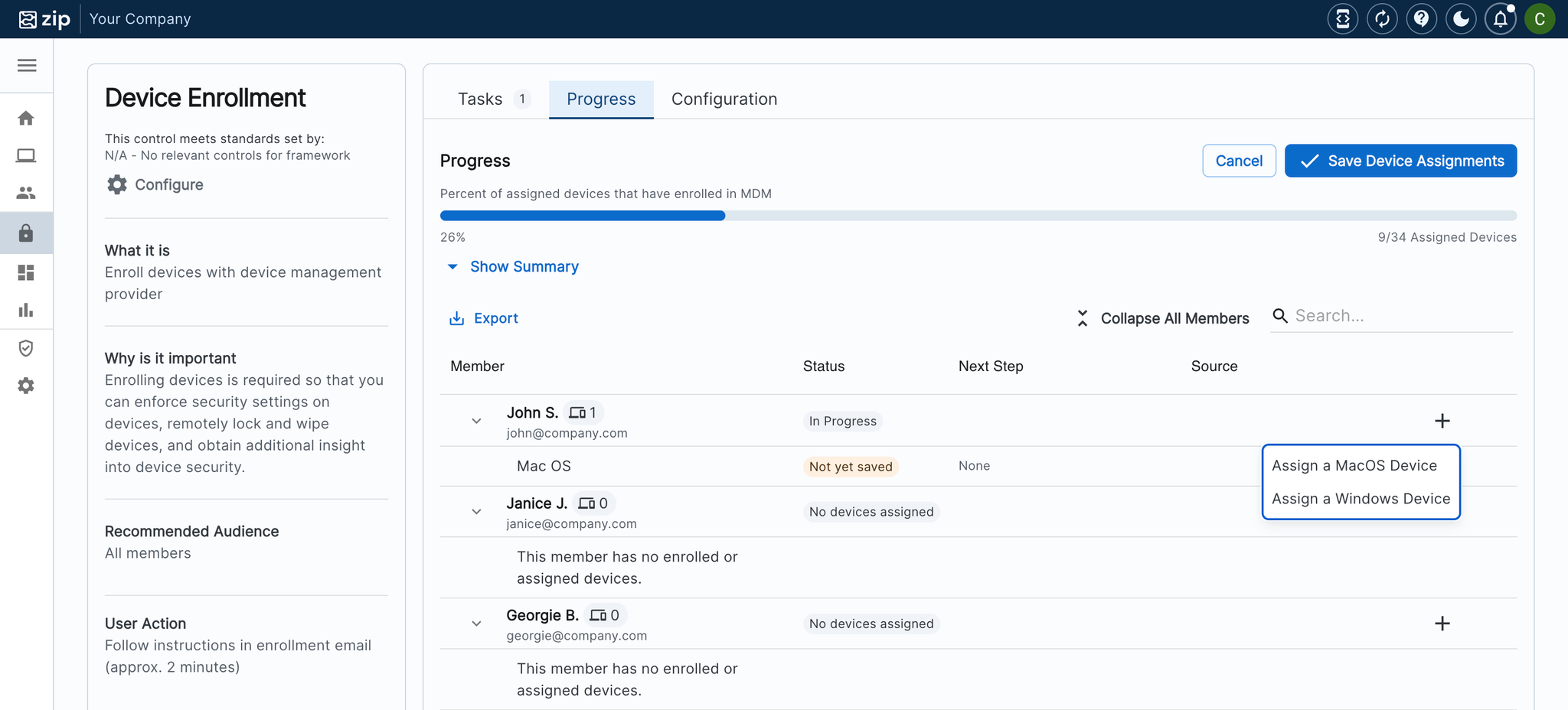
With our new control, apps will automatically land in your Watchlist, making it easy to explore their activity or give the green light to those you trust. Stay in control and keep your data secure, all with just a few clicks!
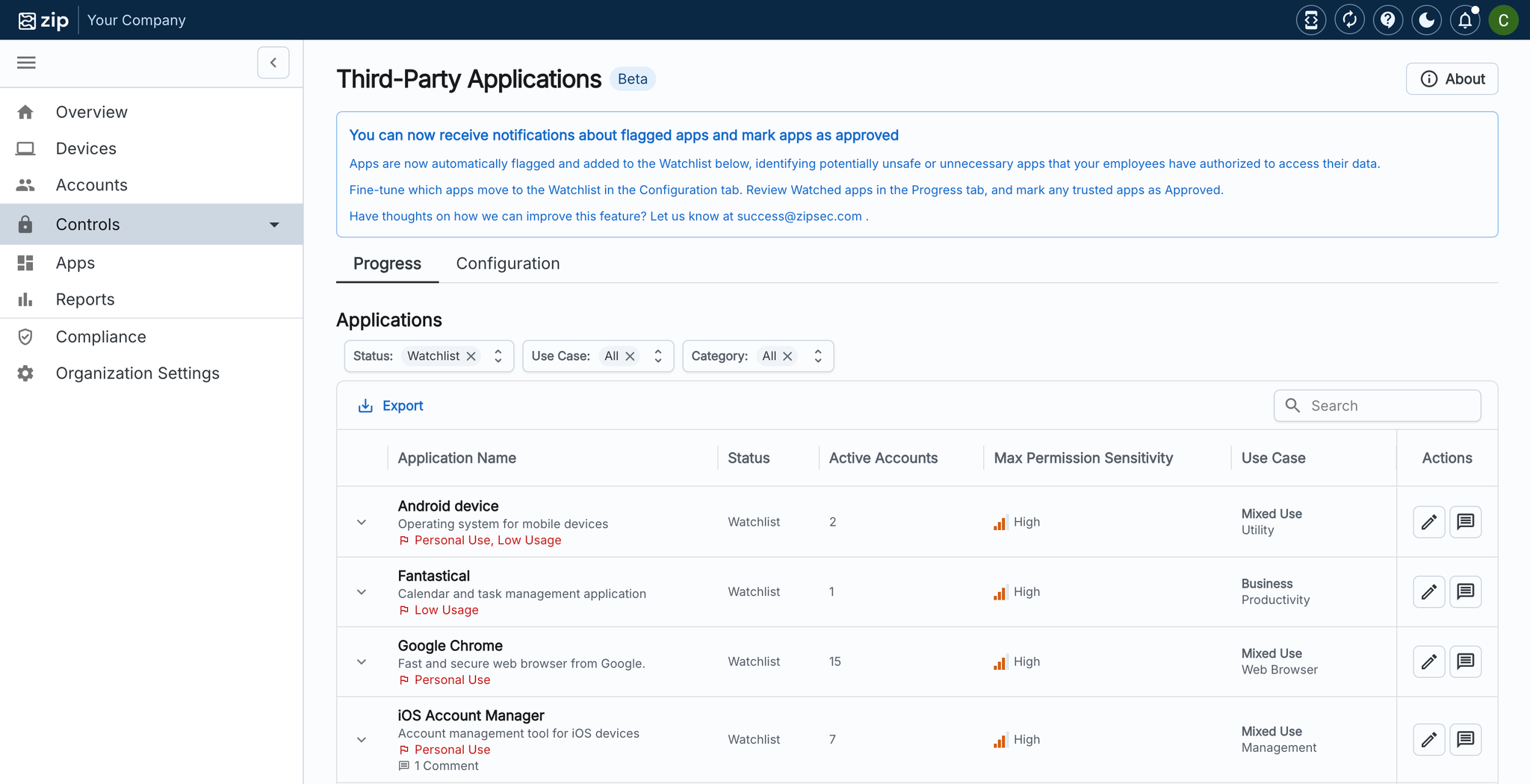
With this latest release, you are now able to:
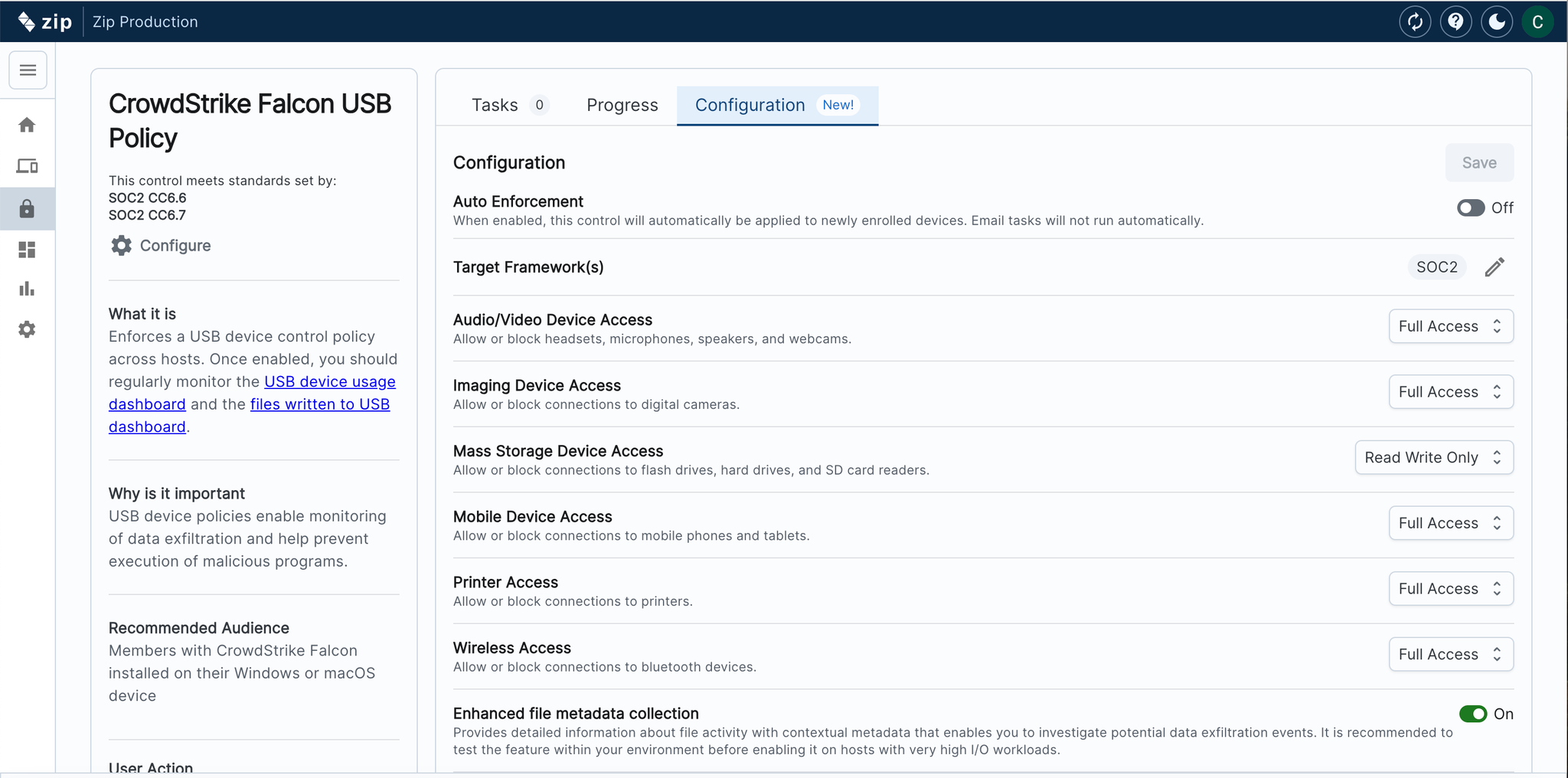
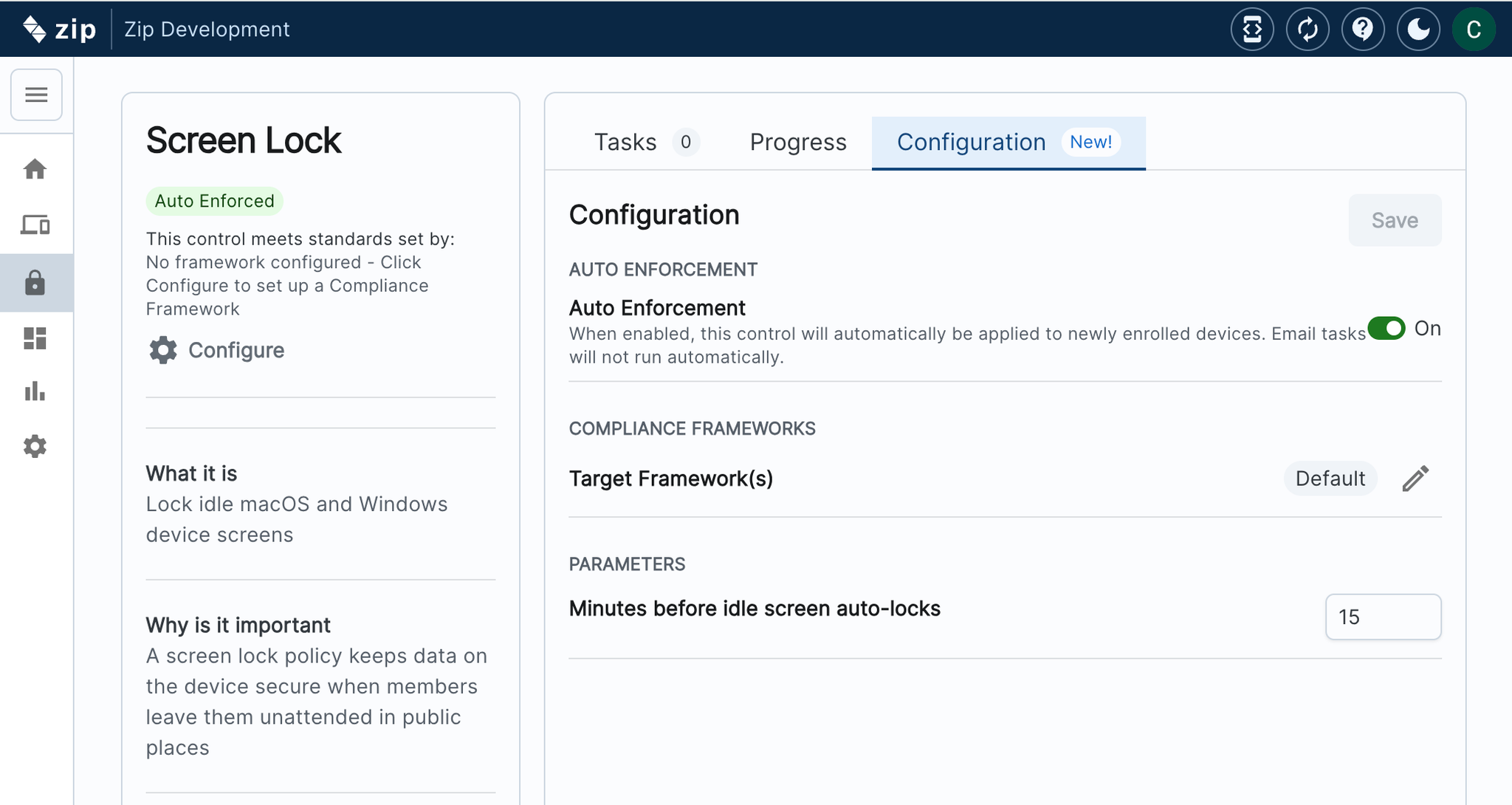
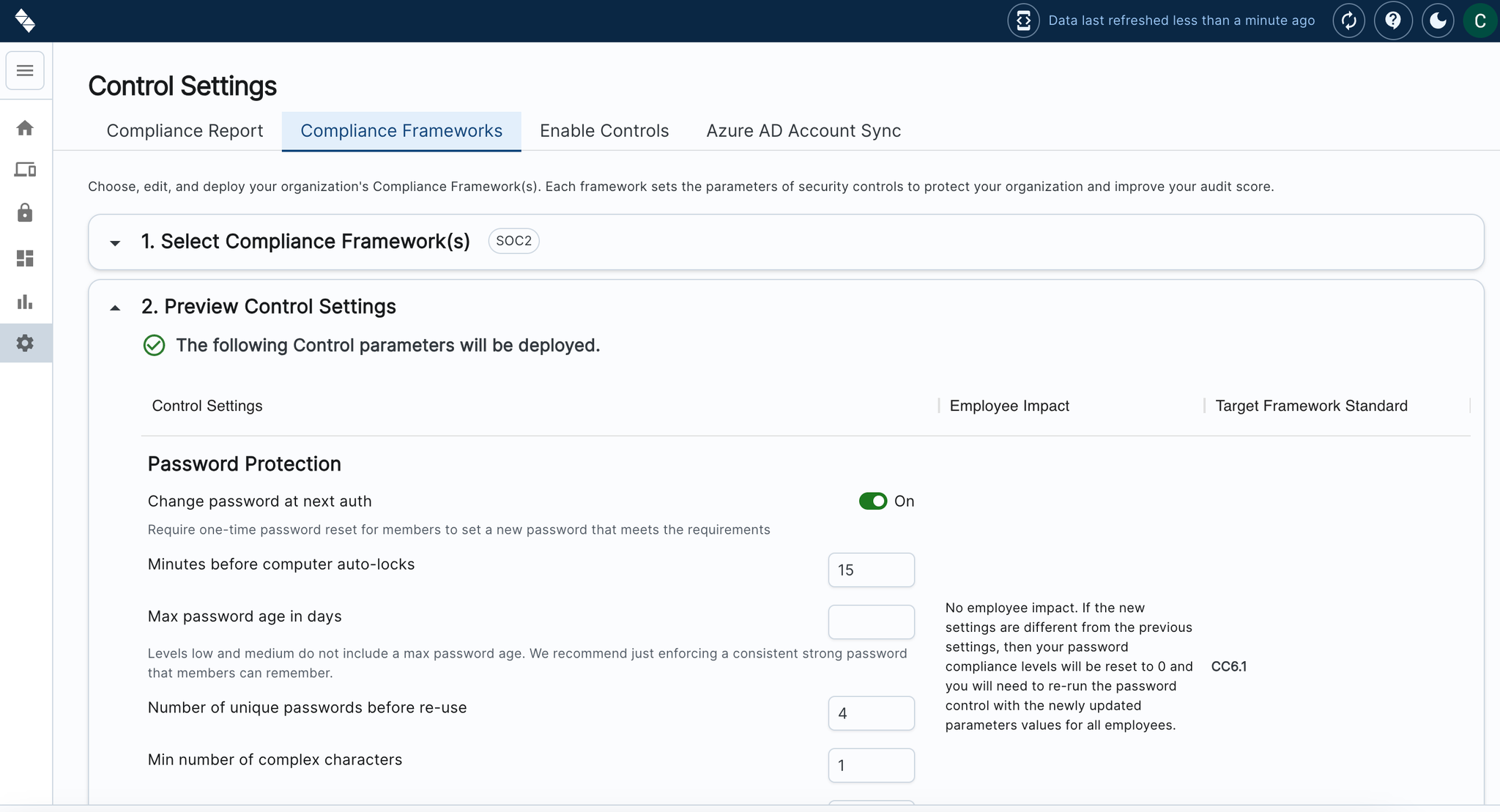
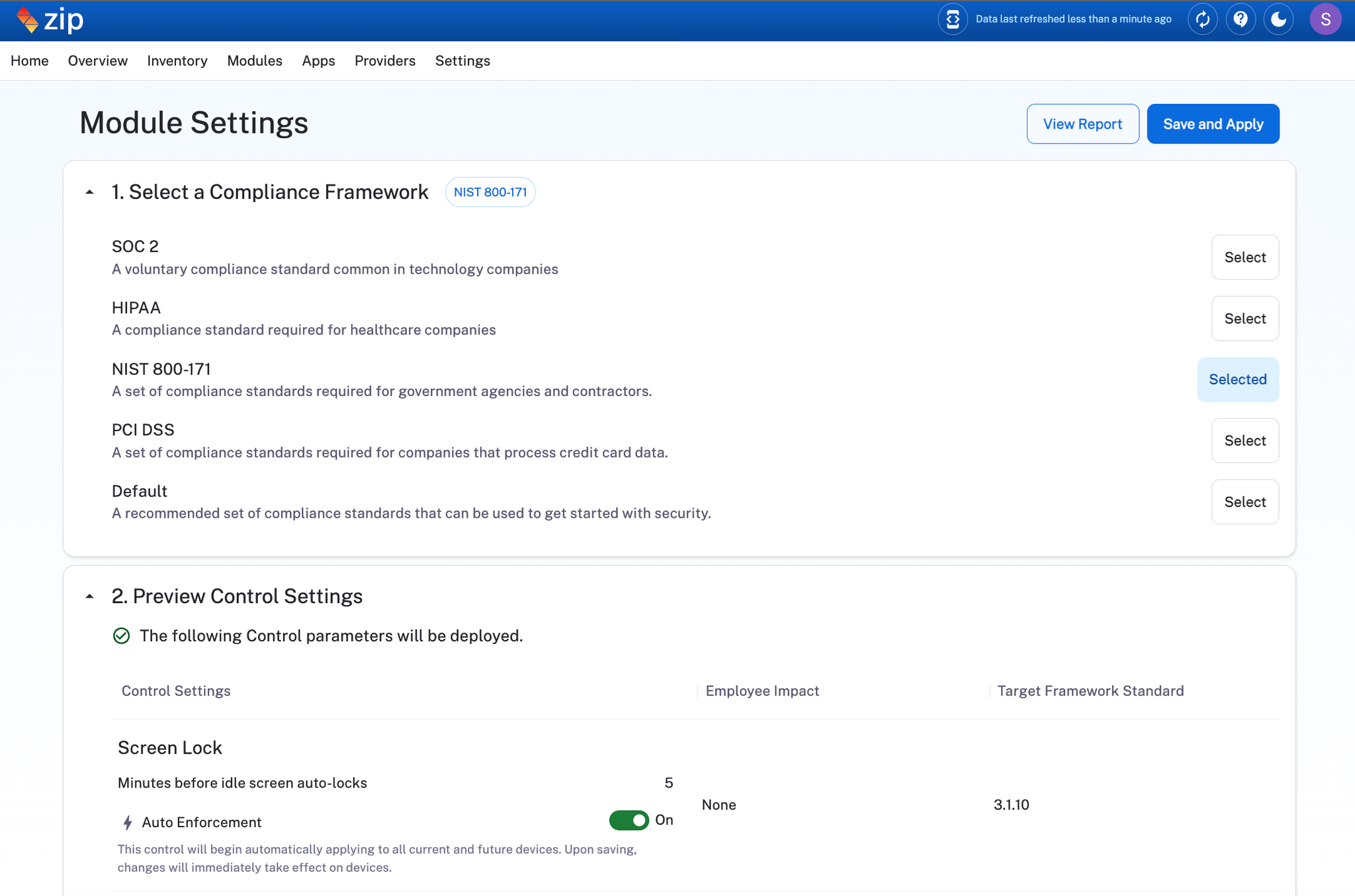
- Set Risk Thresholds in the Configuration Tab: Define custom risk thresholds for applications, allowing the system to automatically scan and flag apps based on your criteria—like low user adoption or personal use. Apps meeting these thresholds will be automatically added to the Watchlist.
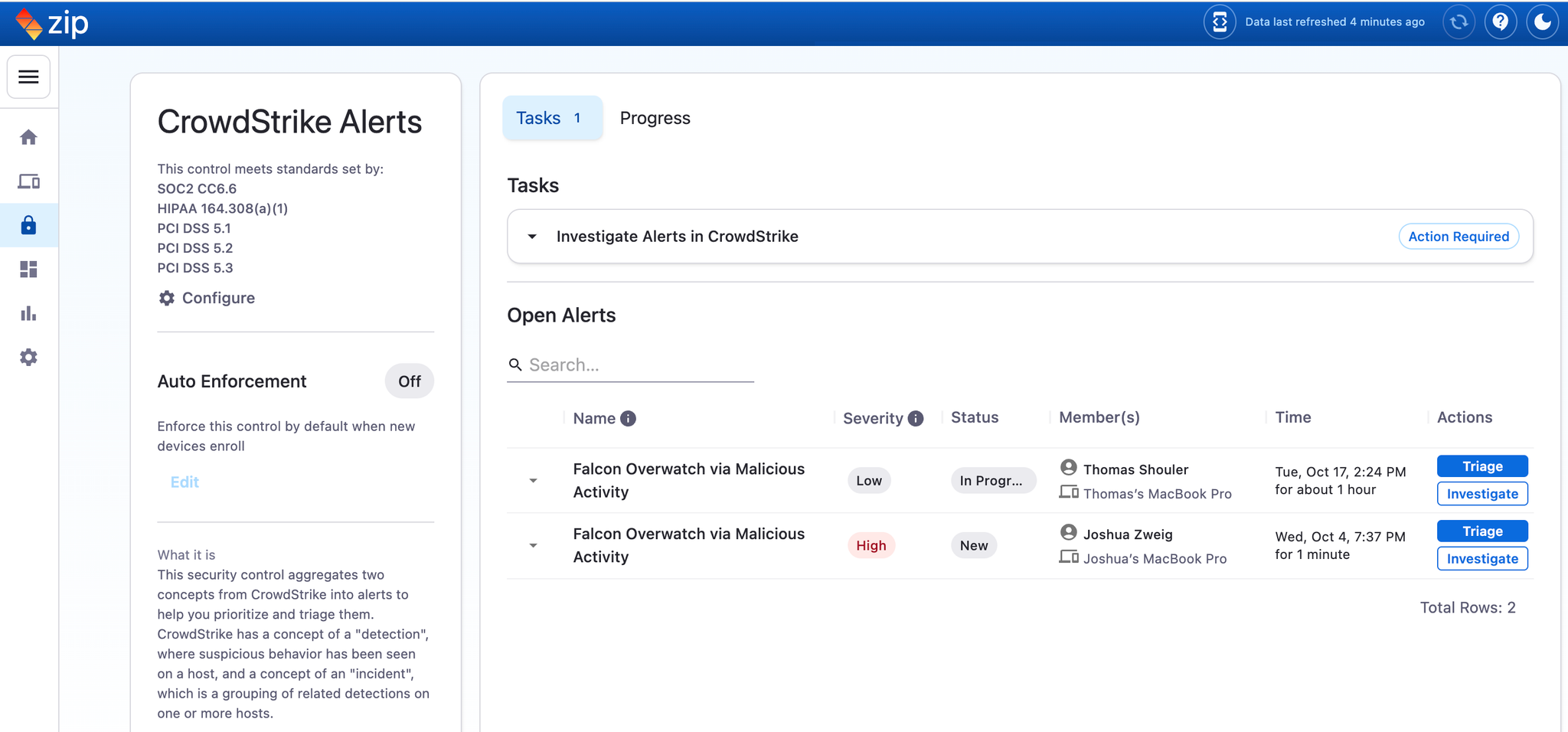
- Triage and Track Applications: Easily update the status of each application to Approved if it is safe or necessary for business use, or work with employees directly to revoke access.
- Add Contextual Comments: Provide additional context by adding comments to each application, streamlining communication and decision-making.
- Receive Real-Time Notifications for Flagged Apps: Get instant notifications whenever new apps are flagged, prompting you to check the console for a closer look.
Why is this great
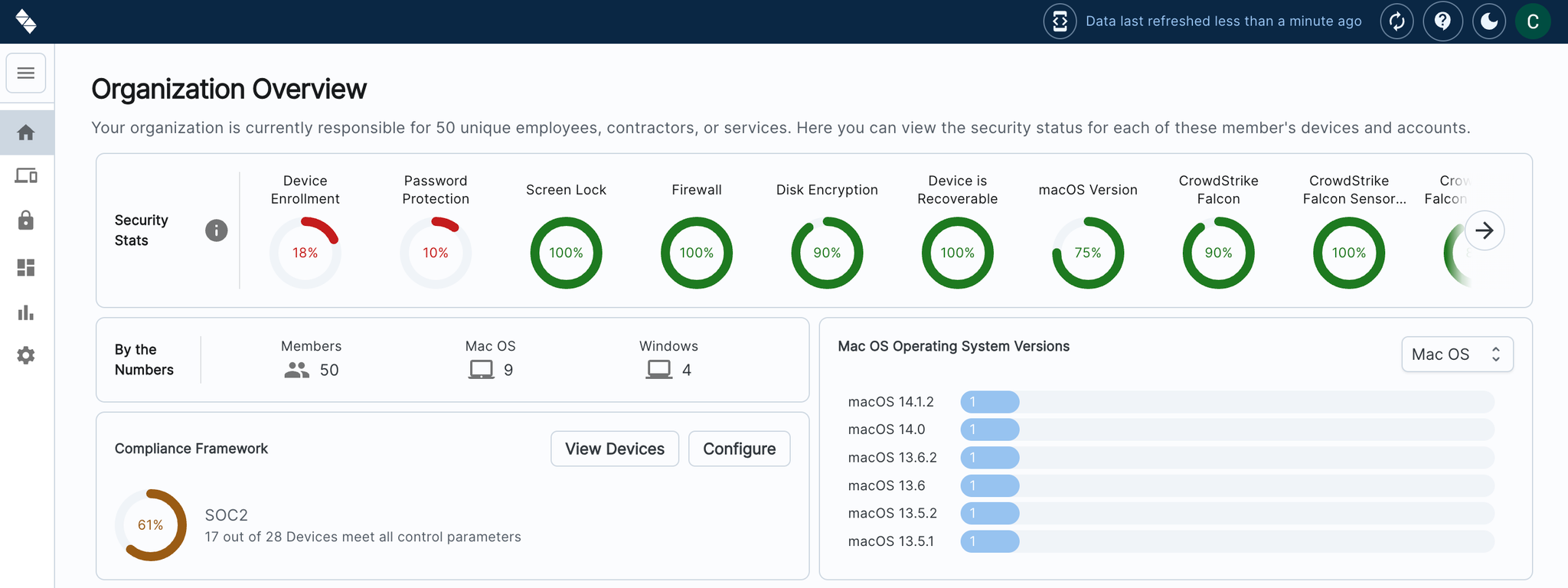
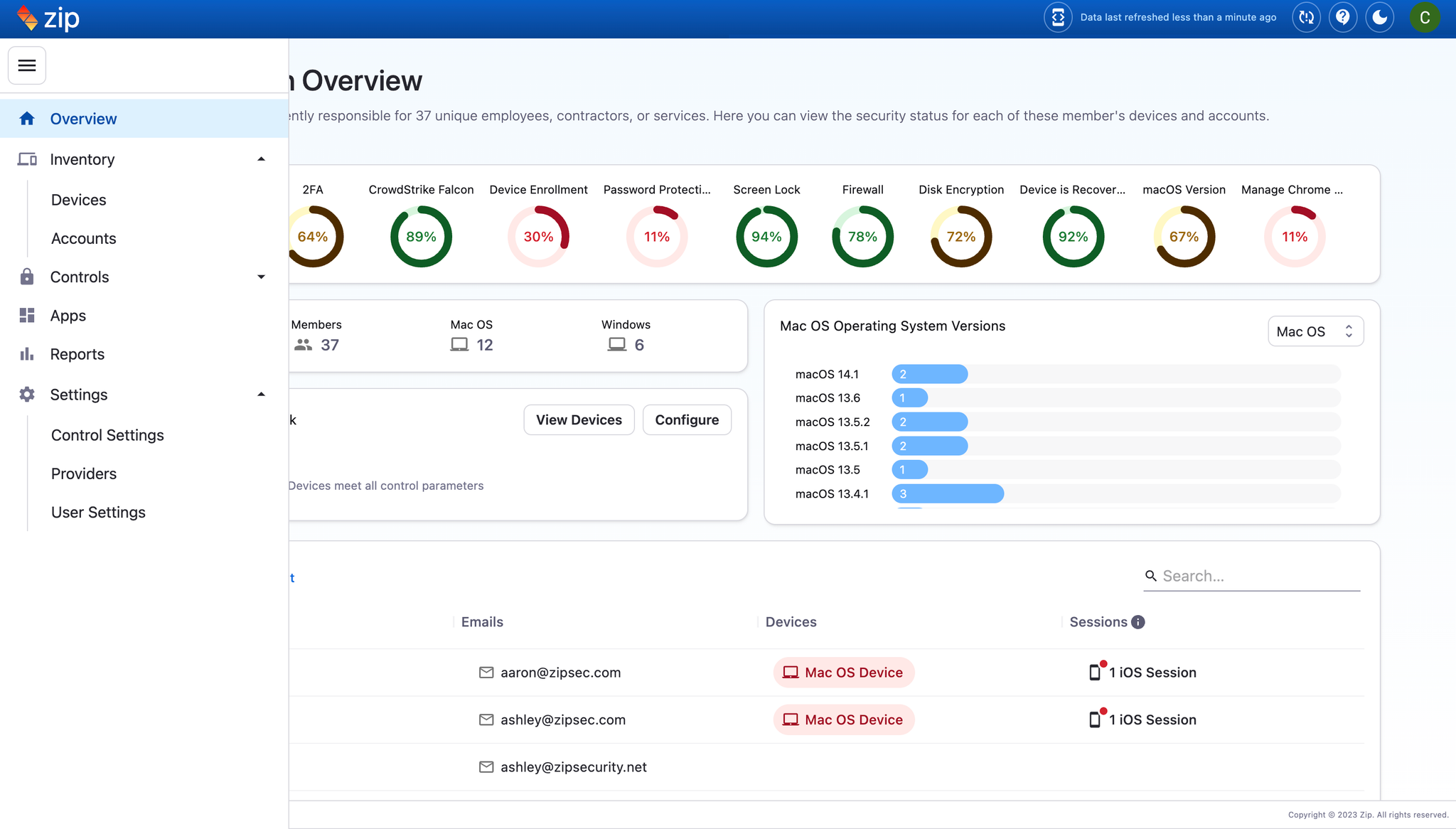
- Enhanced Visibility: Get real-time insights into third-party apps accessing your data, making it easier to identify and manage potentially risky applications.
- Configurable Settings: Tailor permissions management to your organization by setting custom risk thresholds, ensuring alerts align with your security standards.
- Proactive Notifications: Stay ahead with instant alerts when new, high-sensitivity apps are flagged, so you can review and manage access promptly.
- Streamlined App Management: By categorizing apps as approved or watched and adding comments, your team can track and document application activity with ease.
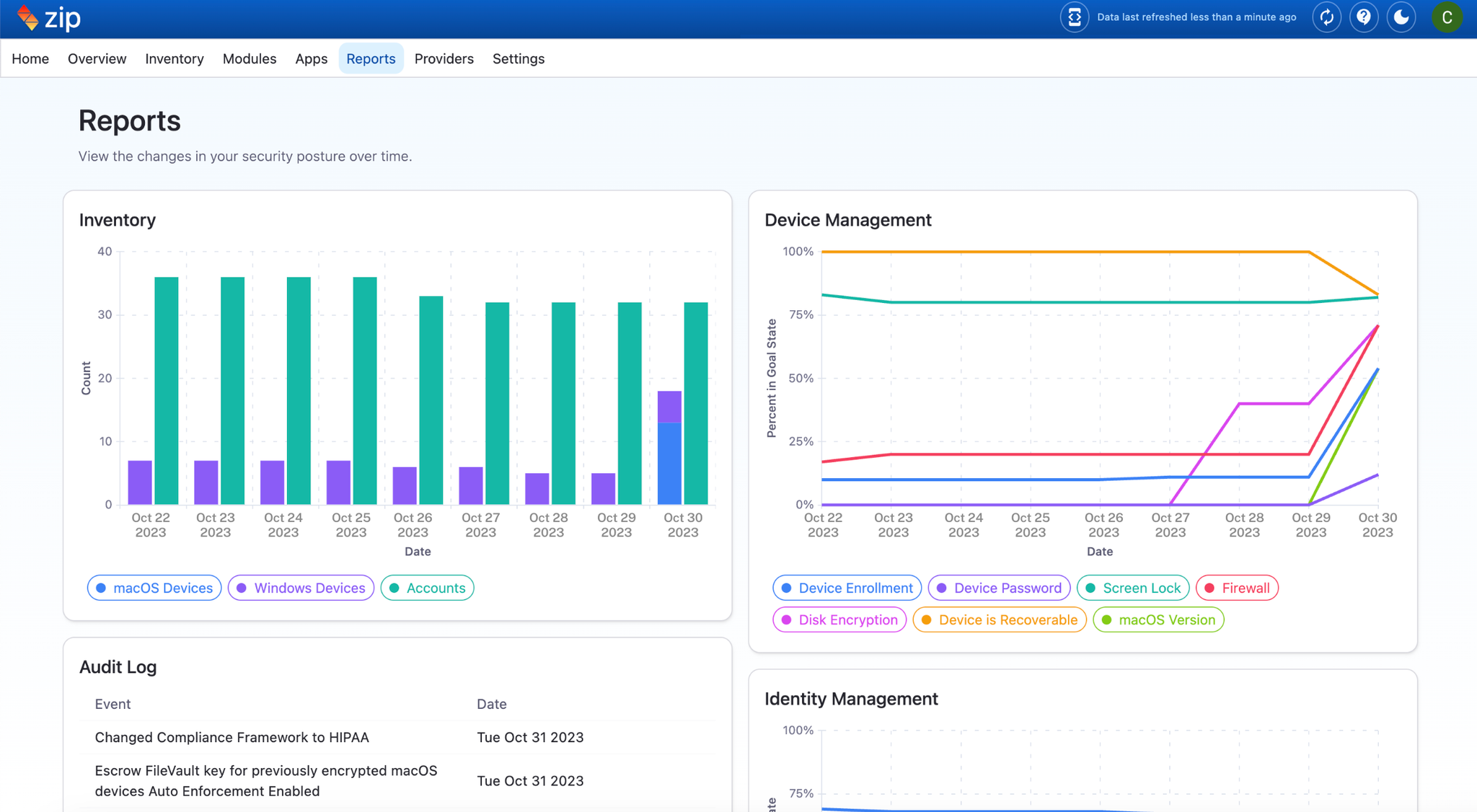
More exciting updates
BCC’ing on emails
Emails you send from the Zip Console are now bcc’d to recipients! This allows you to send communications to team members without exposing the full list of recipients to everyone, offering a more polished experience overall.
One-click login
You may notice that logging into the Zip Console feels a little bit smoother. We’ve shortened the flow so that you can simply continue with email straight from the first step.
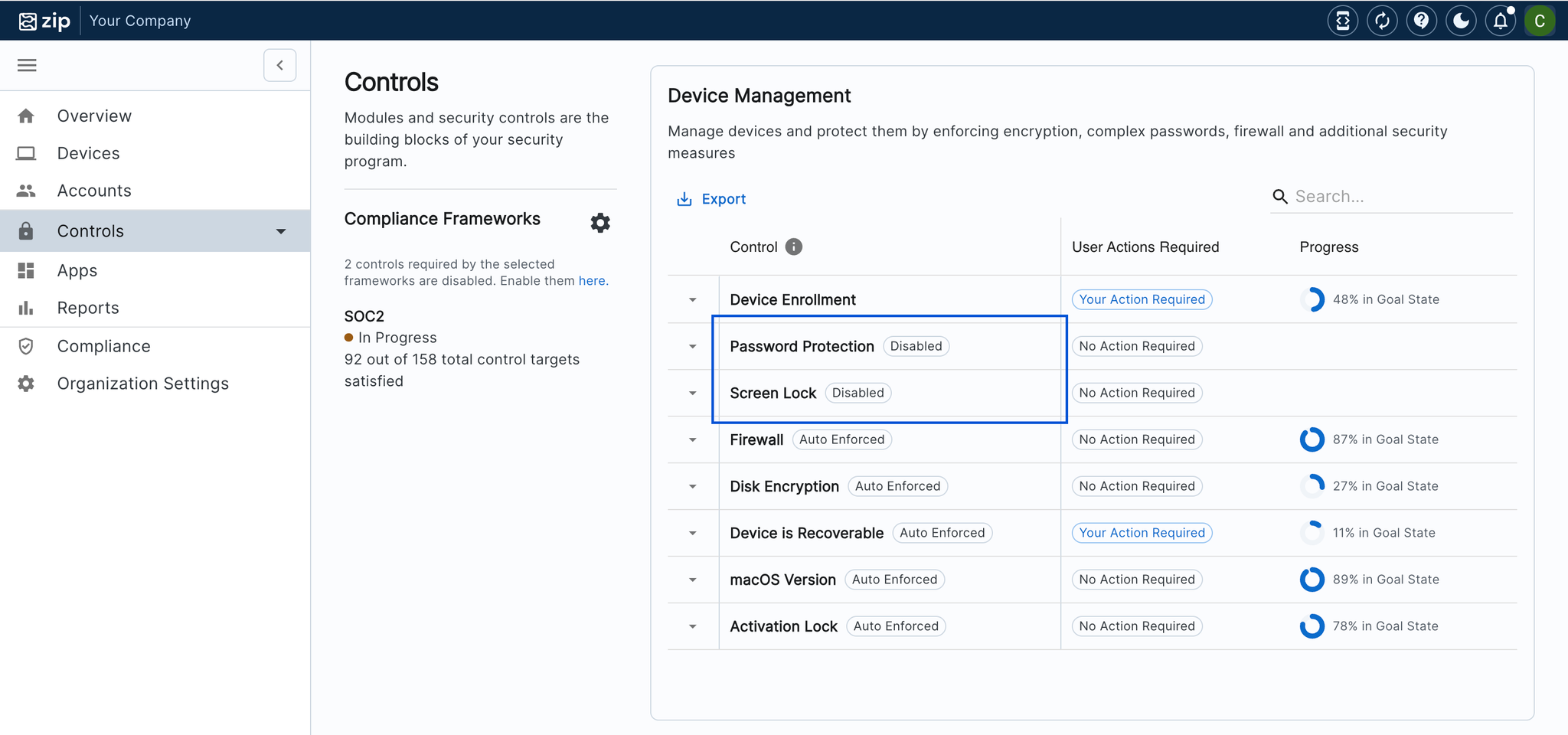
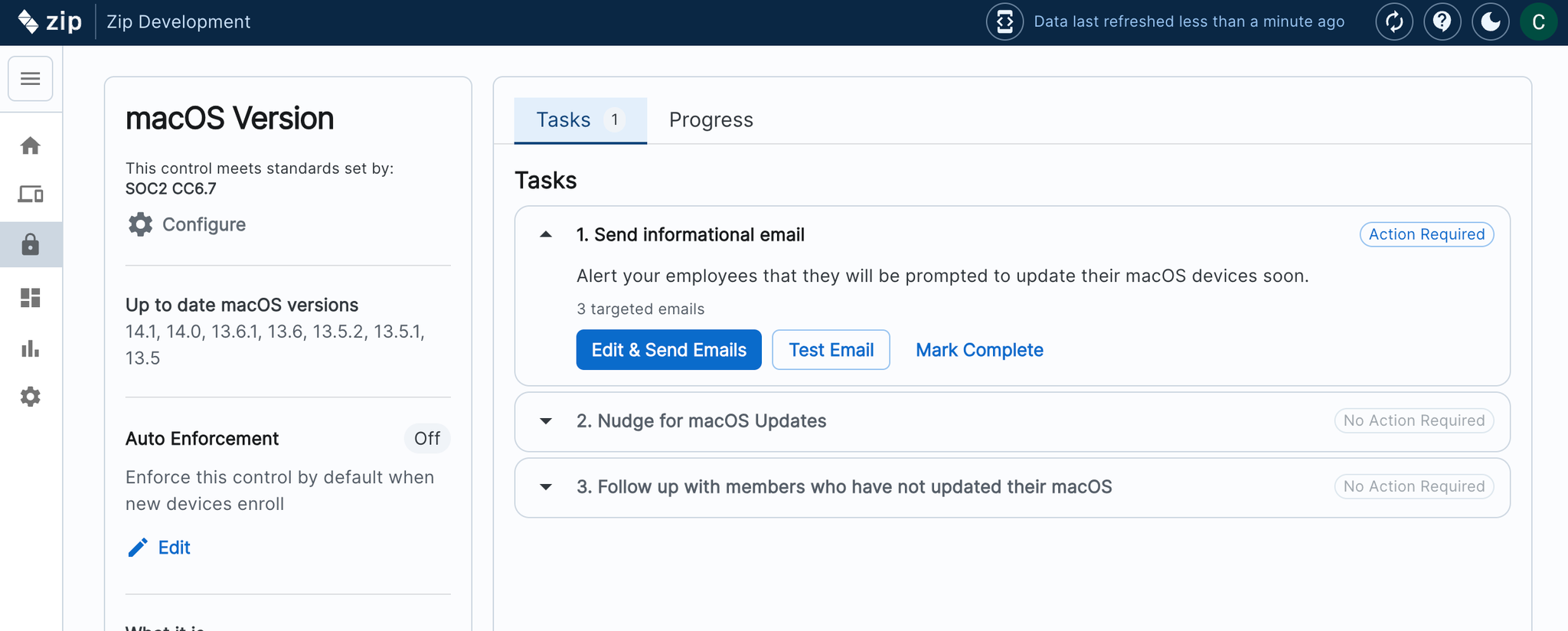
Cleaned up Controls experience
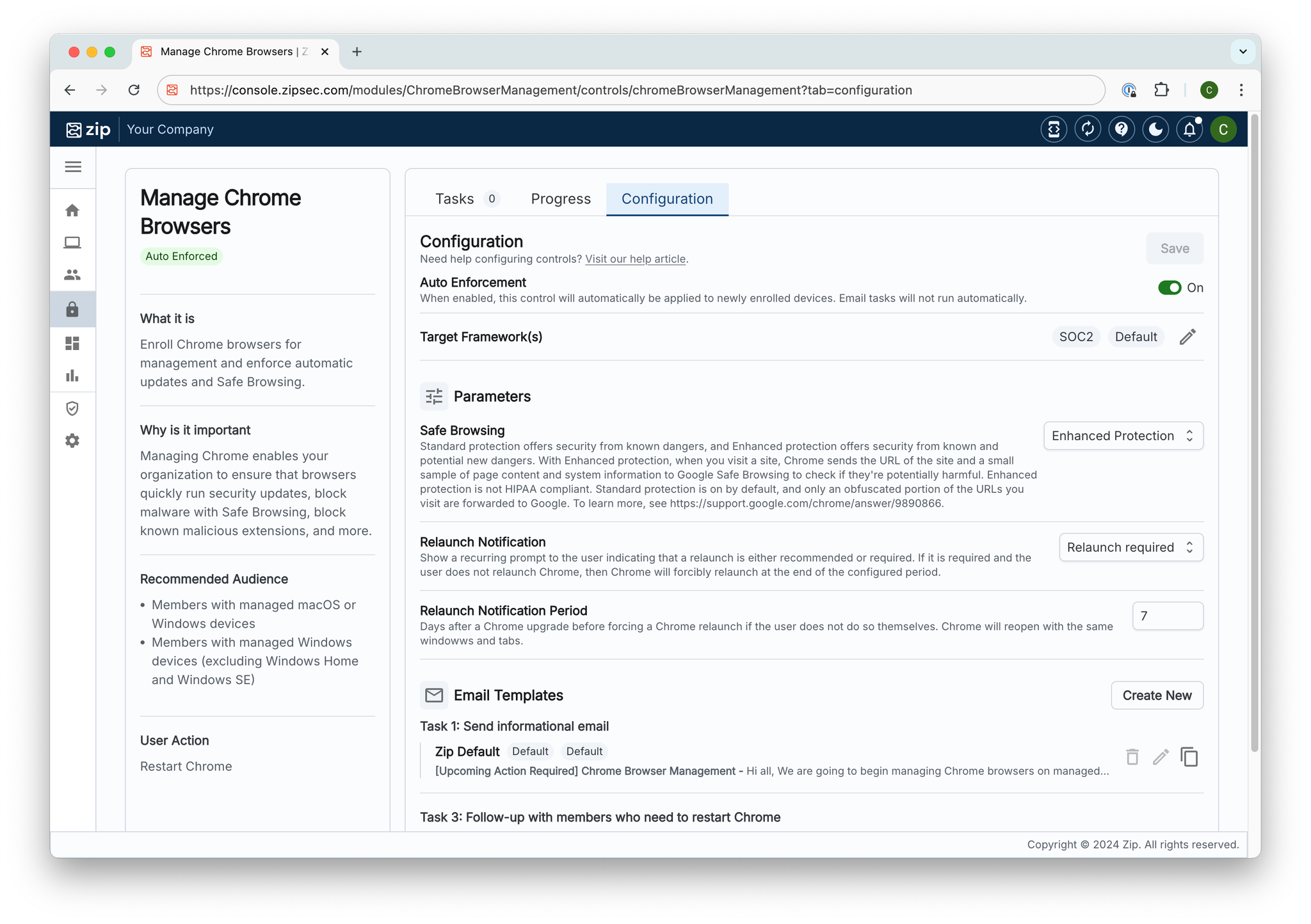
Our controls have an updated look, consolidating essential information and saving you clicks. Look out for more improvements in the coming weeks!
Polished macOS update reminders
We’ve updated macOS update reminders to include more information and Zip branding to increase trust and encourage updating without deferring.